To comprehend how data is exchanged between computers, researchers have adopted the OSI (Open Systems Interconnection) model as a theoretical framework. The International Organization for Standardization (ISO) developed it in the 1980s, and it has since evolved into the benchmark for computer networking. The OSI model has seven layers, each of which has a unique purpose and set of protocols.
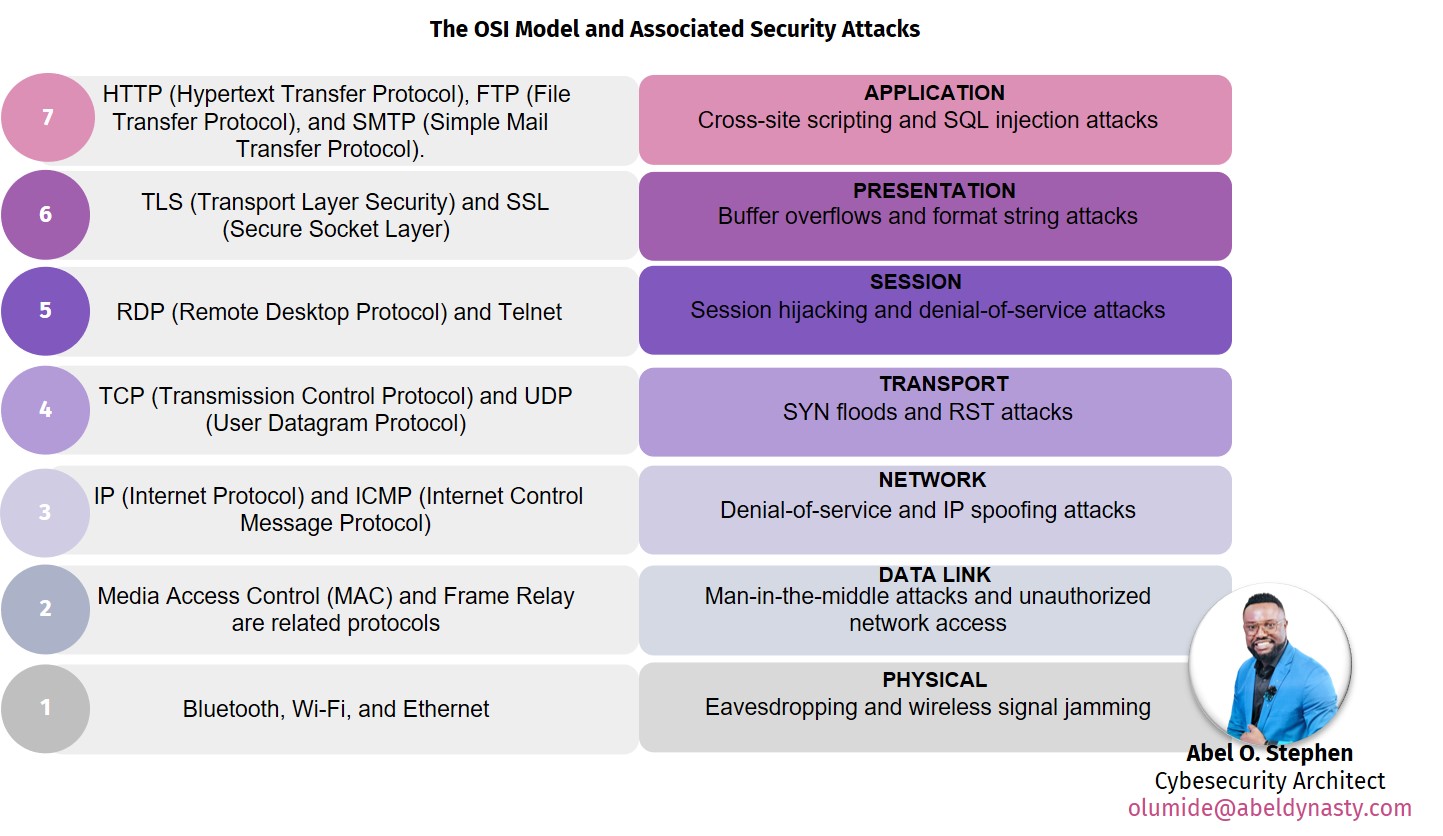
The Physical Layer, the bottom layer in the OSI architecture, is in charge of sending unprocessed data through a physical channel, like a wired or wireless link. Bluetooth, Wi-Fi, and Ethernet are related protocols. Eavesdropping and wireless signal jamming are two security threats that can be made at this layer.
The Data Link Layer is in charge of dividing the raw data into frames and ensuring that each frame is correctly sent. Protocols here are Media Access Control (MAC) and Frame Relay . Man-in-the-middle attacks and unauthorized network access are examples of security assaults that can occur at this layer.
Network Layer: The Network Layer is in charge of directing the frames between various network nodes. IP (Internet Protocol) and ICMP (Internet Control Message Protocol) are associated with this layer. This layer of security is susceptible to denial-of-service and IP spoofing attacks.
The Transport Layer is in charge of making sure the data is transmitted accurately and in the right order. Associated protocols are TCP (Transmission Control Protocol) and UDP (User Datagram Protocol). SYN floods and RST attacks are two examples of security attacks at this layer.
Establishing, maintaining, and terminating connections between devices is the responsibility of the session layer. RDP (Remote Desktop Protocol) and Telnet are two related protocols. Session hijacking and denial-of-service attacks are two types of security threats that can occur at this layer.
Data conversion into a format that the application layer can understand is the responsibility of the presentation layer. TLS (Transport Layer Security) and SSL (Secure Socket Layer) are implemented here. Buffer overflows and format string attacks are just two examples of security vulnerabilities at this layer.
Application Layer: As the top layer in the OSI architecture, the Application Layer is in charge of giving programs access to the network. HTTP (Hypertext Transfer Protocol), FTP (File Transfer Protocol), and SMTP (Simple Mail Transfer Protocol) are protocols related to the layer. Cross-site scripting and SQL injection attacks are examples of security flaws that can be present at this layer.
The OSI model offers a helpful foundation for comprehending how data is exchanged between computers, in conclusion. Security attacks can happen at any layer of the model, each of which has a distinct purpose and corresponding protocols.
Network administrators must be aware of potential security risks and take precautions to safeguard their networks from intrusion.
